Countdown

Walkthrough
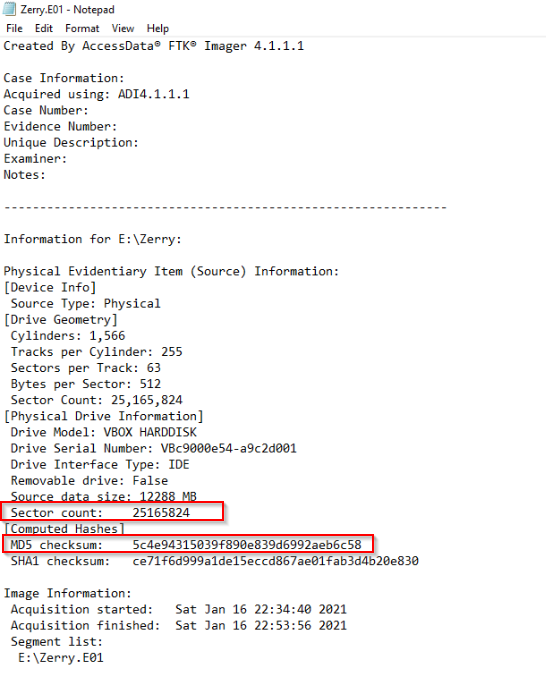
In this investigation, we have two files, a disk image and a text file. By reading it, we learn that the disk image was generated using Access Data FTK Imager.
From that same file we also have all information for the first question:
Investigate Autopsy results
Now let’s analyze the disk image witn Autopsy. To gain some time, a case already exist with provided analysis results:
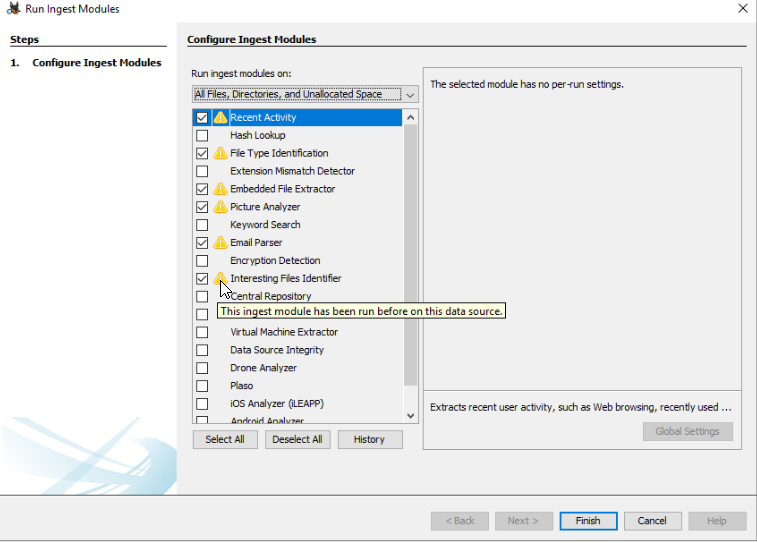
Let’s see the modules that were used for the analysis to have a better ideas with the artifacts available to us. For that, we can check the ingest modules:
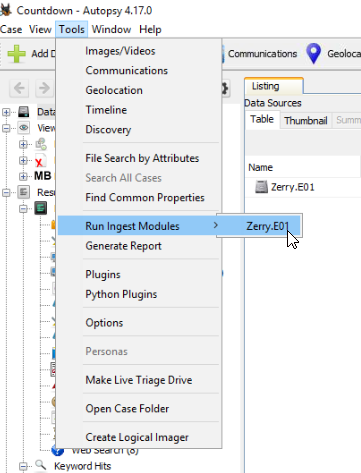
The autopsy modules that were used are the following ones:
To find the decryption key for the online messenger app, I first needed to know what application it was refering to.
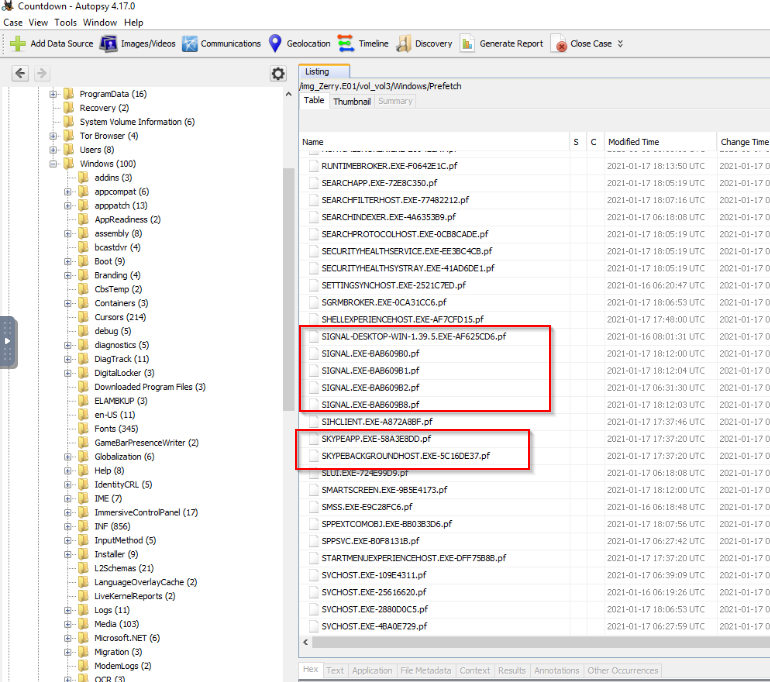
I first checked the Installed Programs in autopsy results, but I didn’t find anything relevant. I then checked the Prefecth directory as per the hints.
From Autopsy we navigate to <C:\Windows\Prefetch> and I noticed two applications that could be good candidates, Signal and Skype:
Access Signal database
After some google searches about retrieving the decryption key from one of the two applications, I found this article.
It appears that the decryption key is stored in clear text in <%AppData%\Signal\config.json> …
In our case the file is located in <%AppData%\Roaming\Signal\config.json>:
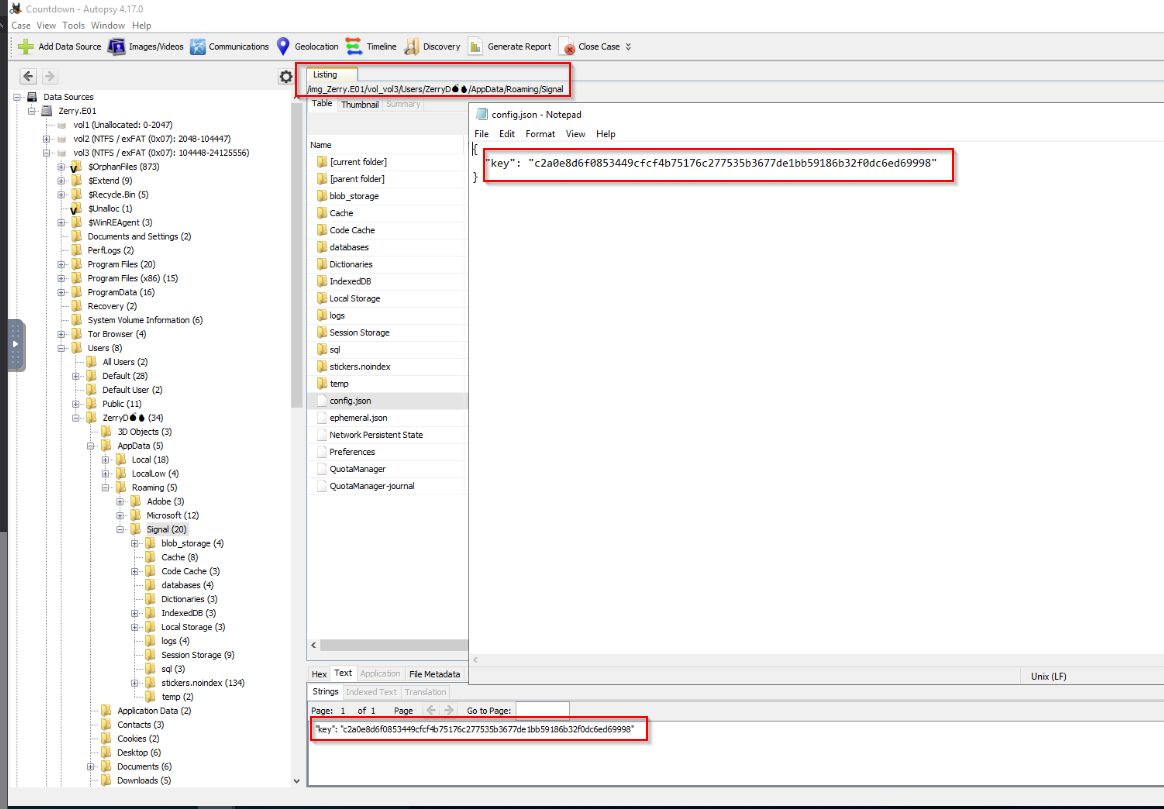
(You can either get the value directly from the Text tab from Autopsy or you can extract the file by right clicking on it.)
Ok, so now that we have a decryption key, we need to use it !
From the same article we learn that the related database is located at <%AppData%\Roaming\Signal\sql\db.sqlite>. Let’s extract this database and try to open it. From the Tools directory, we have the utility SQLite Database Browser Portable.
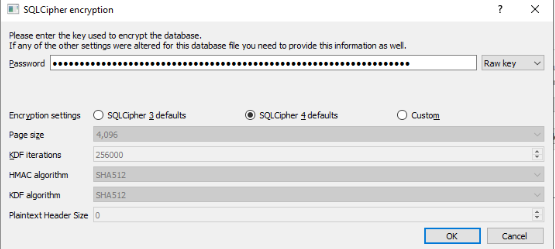
Since we don’t have the passphrase, we need to select Raw Key:
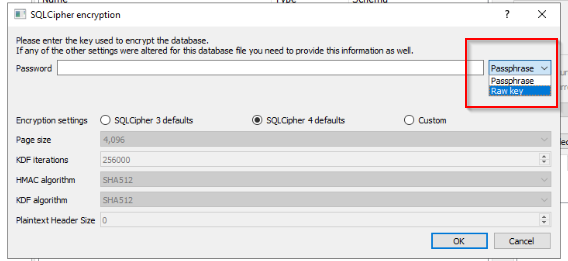
Once selected, you’ll notice that the background text change with 0x…, this means that we need to put 0x at the beginning of the key (you won’t be able to paste the key otherwise, took me a while to realise it…):
We can then decrypt the database with the default options:
In the database we find a conversation:
From the related metadata, we get more information regarding the user:
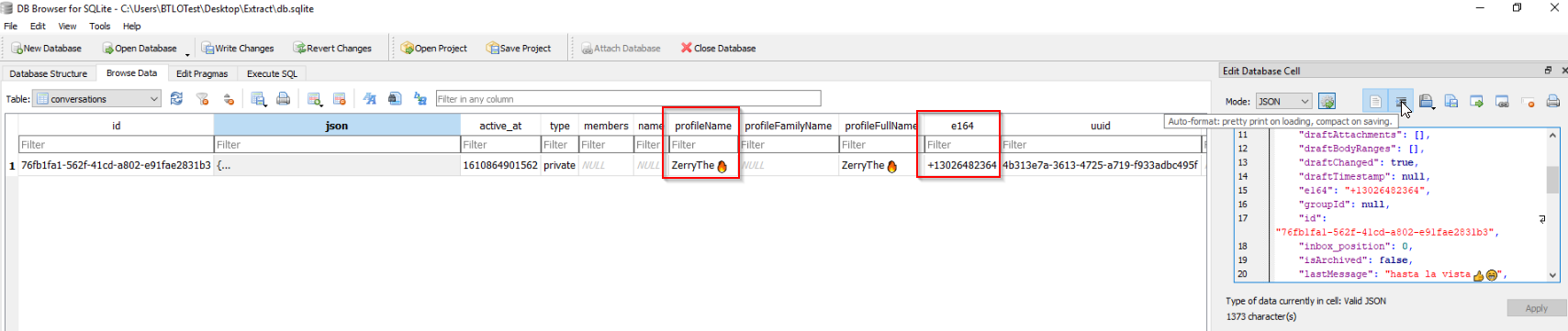
13026482364,ZerryThe🔥
Note: There are a lot of emojis in this challenge, and they are required in the answers. For that I used this website.
By reviewing the related messages, we can see two friends (Tom and Jerry!) talking about their plan to bomb a city. We also find an email address:
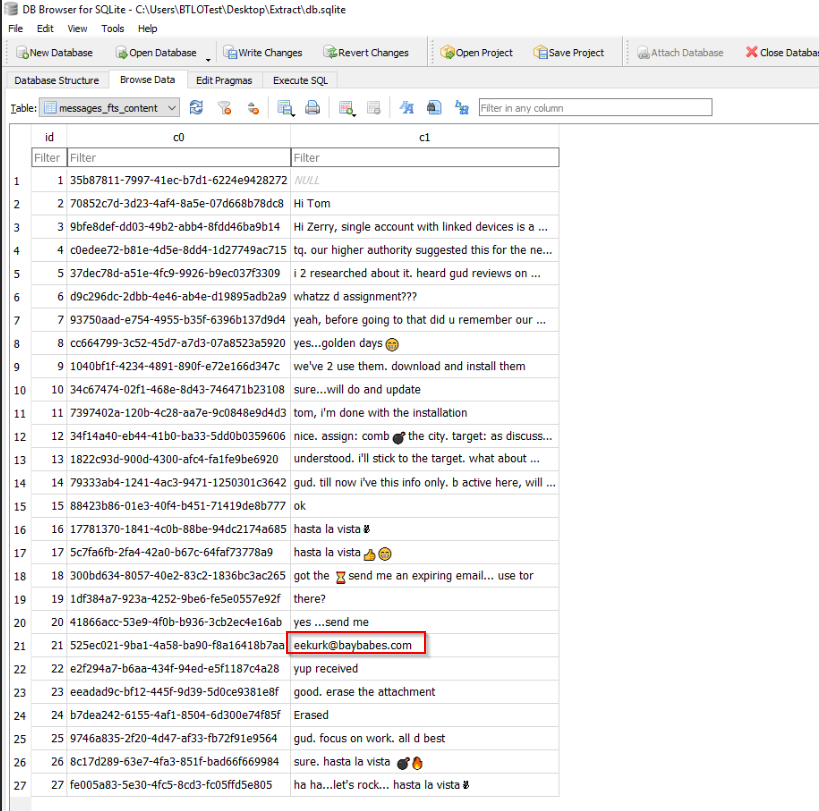
We also learn that an email was sent with an attachment, which was then erased.
Finding the email attachment
When reviewing the recent documents from Autopsy, we notice a .lnk file with a strange name.
According to the previous converstaion, the same “time” emoji was used:
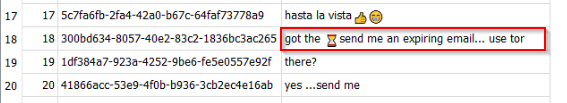
It is more likely that this shortcut is related to the file attached to the email.
As per the hints, since the file is an image, we can check the Thumbcache. This data is stored in a .db file, we can access it directly from the File Types view and extract it:
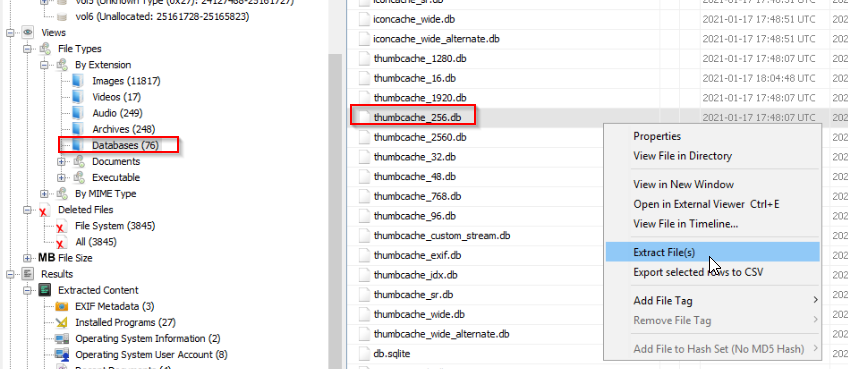
The tool Thumbcache Viewer is provided, let’s use it ! Once opened, we have multiple results. if we filter by data size we notice that only 2 images have a size different than zero (if you extract all results, you will only get two files).
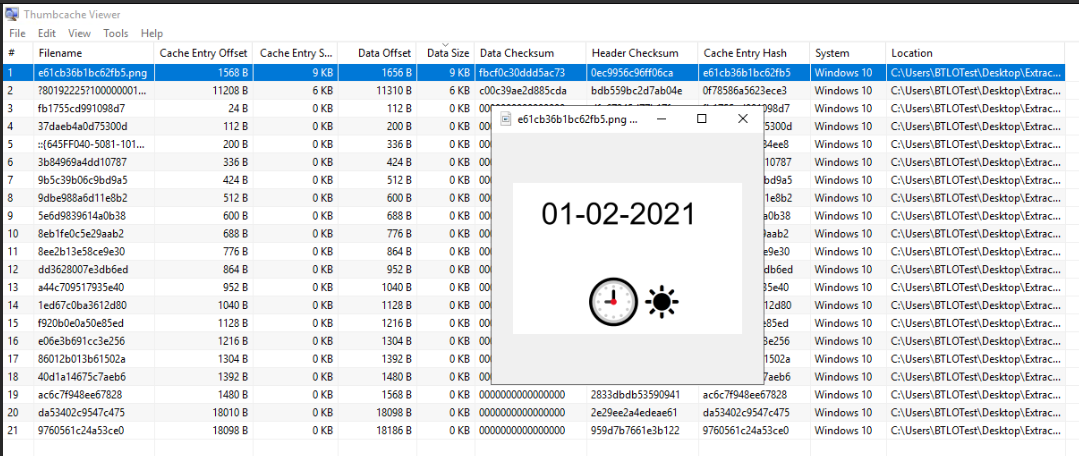
If we preview the first one, the image shows a date, with a little sun specifying that the hour is in the morning:
Locate the attack
Now that we have the time of the attack, we need to know where it will occur !
According to the hints, the location is stored in a Sticky Note. They are stored in a database called plum.sqlite. Again, we directly accessed it from the Databases file type and extract it.
Inside the database we find a note that seems to be a GPS location but the content is encoded.
| |
As per the hint, we review the user Tor browsing from the places.sqlite database to know more how it was encoded.
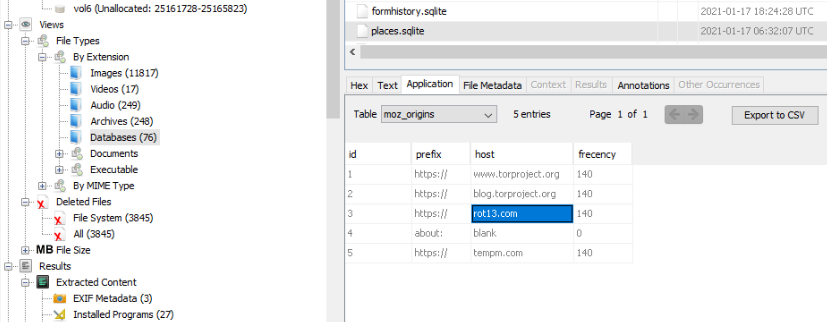
We just need to apply the ROT13 algorithm and we get the GPS coordinates.
Final notes
This investigation was the only one available during the private beta, in which I managed to get the first blood !
I wasn’t fast enough with the copy/paste on the official release date to get it back though :p