Bypass Address Space Layout Randomization (ASLR)
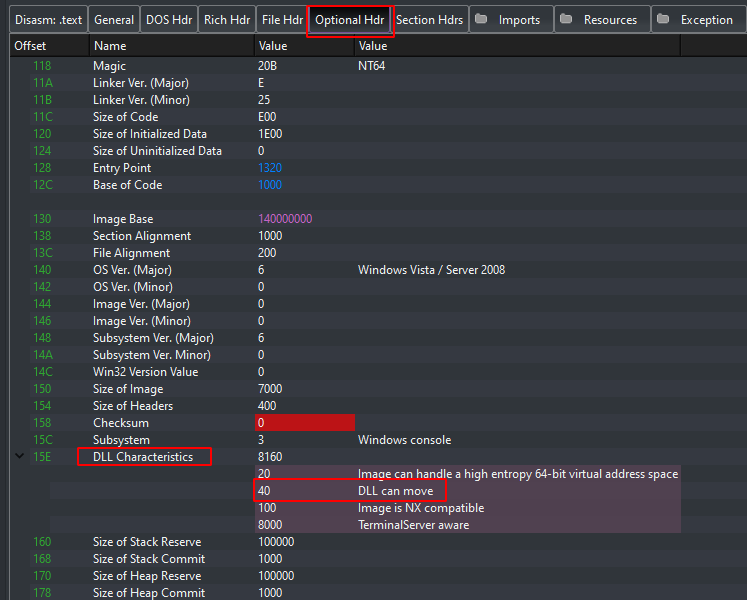
DLL Characteristics
To know if a PE file will use ASLR, you can check the DLL Characteristics in the Optional Header PE headers. If the field contains the value 0x0040( cf Microsoft Documentation - DLL characteristics), it means that the image base address can be relocated at load time.
For example, if we check with PE-bear:
Rebase in Ghidra
If you are working on a sample in both a debugger and a disassembler, you can modify the image base address of the binary in the disassembler to have the same alignment than the one from memory found in the debugger.
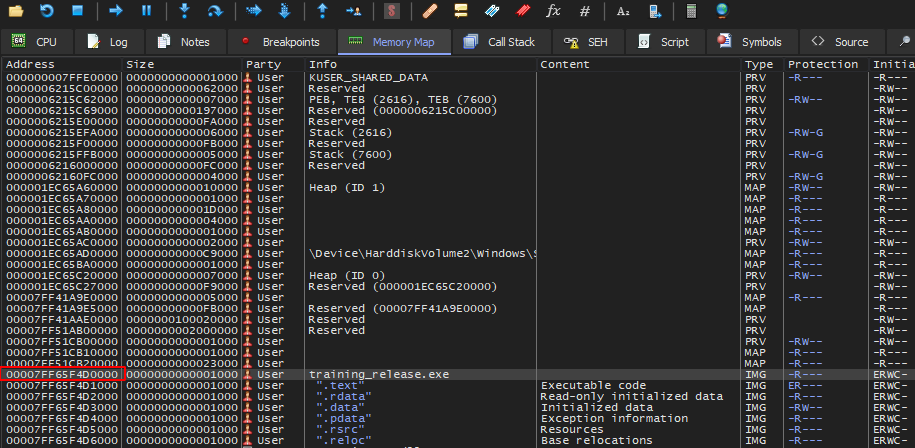
First, find the virtual address in the debugger. In x64dbg, go to Memory Map, and then find the address related to the name of the sample:
In Ghidra, go to Window -> Memory Map: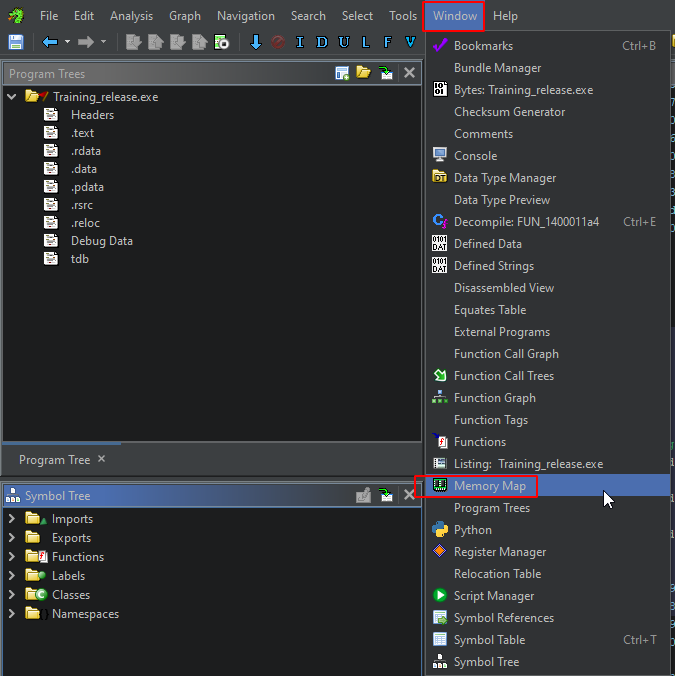
Then click on the Home icon and specify the address in the new window: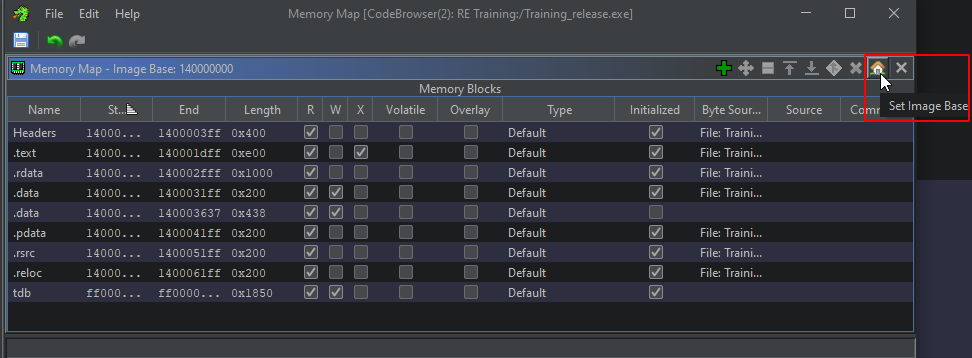
each DLL or EXE image gets assigned a random load address by the kernel the first time it is used, and as additional instances of the DLL or EXE are loaded, they receive the same load address. If all instances of an image are unloaded and that image is subsequently loaded again, the image may or may not receive the same base address. Only rebooting can guarantee fresh base addresses for all images systemwide.Disable ASLR at Operating System level
In Windows, you can disable ALSR by going into the Exploit Protection security settings windows and disable all ASLR related settings: